Value of an OCR-Quality Risk Analysis® Has Never Been Higher
Many Chief Information Security Officers and Chief Compliance Officers often express concern to us about the potential disruption and cost that can come from an Office for Civil Rights (OCR) investigation, not to mention the reputational damage that will result from a settlement or monetary penalty. An appearance on the wall of shame is a mere blemish compared to the negative publicity of an OCR fine or settlement. However, the possibility of a State Attorney General (AG) action is often underestimated and overlooked. If a State AG enforcement is not top of mind for you and your board, it should be.
State AGs are becoming much more active, and now banding together to initiate multi-state suits. They are following OCR’s lead, and bringing their own actions on healthcare organizations that have violated HIPAA regulations, most recently in cases where there has been a failure to conduct a risk analysis of all information systems that maintain, receive, create, or transmit ePHI.
Let’s review the history of State AG enforcement.
OCR has been encouraging State AGs to activate their authority to bring civil actions on behalf of state residents for violations of the HIPAA Privacy and Security Rules since the 2009 passage of section 13410(e) of the HITECT Act in 2009. In fact, OCR promised to:
- Collaborate with State AGs seeking to bring civil actions to enforce the HIPAA Rules
- Provide guidance regarding the HIPAA statute, the HITECH Act, and the HIPAA Privacy, Security, and Enforcement Rules as well as the Breach Notification Rule
- Assist State AGs in exercising this new enforcement authority by providing information upon request about pending or concluded OCR actions against covered entities or business associates (BA) [1]
OCR even provided training modules for State AGs on its website. [2] But it’s taken a little bit of time for State AGs to get actively involved, although some have been more active than others.
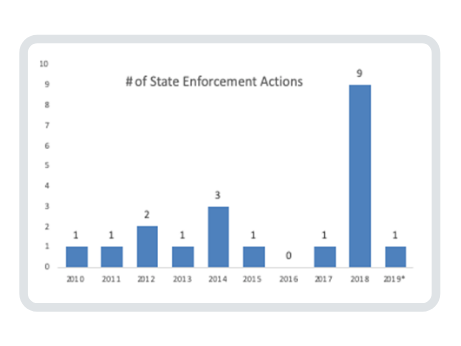
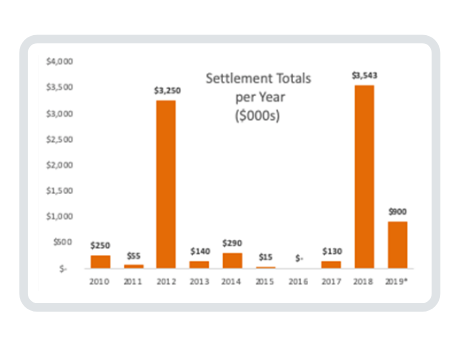
Earliest Enforcement
The earliest HIPAA enforcement action was undertaken in 2010 by the AG of Connecticut against Health Net, Inc. for the theft of a portable hard drive and notification delay. 446,000 Connecticut residents were affected costing Health Net $250,000. In 2011, the AG of Vermont also took action with Health Net for $55,000 on behalf of 525 of its residents.
Activity picked up a little bit in 2012. The Minnesota AG settled a lawsuit with Accretive Health for $2.5 million for sharing patient information of 23,000 residents without a Business Associate Agreement and banned the company from operating in Minnesota for two years. The Massachusetts State AG fined South Shore Hospital $750,000 on behalf of 800,000 residents for providing unencrypted data tapes to a subcontractor to erase and resell.
The Massachusetts AG was now on a roll. In 2013, she fined Goldwait Associates $140,000 for throwing health records of 67,000 residents into a public dumpster. Then in 2014, three more enforcement actions were taken by the Massachusetts AG:
- $150,000 settlement with Women & Infants Hospital of Rhode Island for lost unencrypted backup tapes from two prenatal diagnostic centers affecting more than12,000 residents
- $100,000 settlement with Beth Israel Deaconess Medical Center for a stolen unencrypted laptop affecting 4,000 residents
- $40,000 settlement with Boston Children’s for a stolen unencrypted laptop affecting 2,160 residents
Later Years
In the following years, the New York AG settled with:
- University of Rochester Medical Center for $15,000 for insufficient training of a nurse practitioner who shared health information of 3,400 residents with a future employer (2015)
- CoPilot Support Services for $130,000 for unauthorized access to health records of 220,000 residents to check insurance eligibility in addition to delayed notice (2017)
- Aetna for $1.15 million for revealing HIV/AIDS status through a mailing label to 2,460 residents (2018)
- Arc of Erie County $200,000 for a BA exposing sensitive PHI of 3,750 residents on the internet for years (2018)
- Emblem Health $575,000 for revealing social security # on mailing labels (2018)
Six more settlements in 2018 included:
- New Jersey AG with:
- Virtua Medical Group $418,000 to settle allegations that it failed to conduct a thorough risk analysis of ePHI it sent to Best Medical Transcription and failed to implement security measures to reduce that risk
- Emblem Health, the second State AG settlement, this time for $100,000. In addition to HIPAA regulations, New Jersey found EmblemHealth violated the state’s Identity Theft Prevention Act and the New Jersey Consumer Fraud Act.
- Massachusetts AG with:
- UMass Memorial Health Care $230,000 for two separate incidents of unauthorized access by employees of PHI belonging to 15,000 residents
- McClean Hospital $75,000 for losing four unencrypted backup computer tapes containing psychiatric information of 1,500 patients
- Yapstone, a payment processor, $155,000 for an unprotected website containing social security numbers
- New York AG with Aetna for a $1.15 million settlement on behalf of 2,460 residents
- The first multistate settlement agreement by AGs in Connecticut, New Jersey, Washington, and the District of Columbia (DC) was reached in October 2018 with Aetna for $640,000
This Year
In early 2019, Aetna was back in the news when California’s AG hit it with a $935,000 fine on behalf of its 1,191 residents. State AG enforcement fines with Aetna now total $2.725 million.
Most recently, Medical Informatics Engineering (MIE) agreed to pay $900,000 in a multi-state lawsuit involving 16 State AGs. The Indiana EMR service business associate didn’t perform a comprehensive risk analysis before its server was hacked in May 2015, breaching the data of 3.5 million patients from several healthcare clients who were residents of the 16 states.
Our View
Patients are frustrated and angry with the number of breaches that are occurring in the healthcare industry. Their frustration and anger are understandable as this is where their most personal and valuable data resides. They expect their providers to protect their data in the same way that they rely on them to protect their health. This is an important issue for constituents and one where we believe State AGs, as well as state politicians, will continue to demonstrate to their residents that they are taking action.
Our prediction is there will be very little mercy shown for any organization that fails to comply with requirements of HIPAA, and especially for those that experience a breach, and are found not to have conducted a risk analysis that might have identified the vulnerability that was exploited.
Our Advice
Clearwater recently had the opportunity to consult on a large State AG lawsuit enforcement action, and so we can offer some perspective based on that experience. Of the 21 State AG enforcement actions, 16 of them (76%) involved ePHI. The only way anyone can understand and prioritize risk mitigation in a cybersecurity program is to conduct a bona-fide OCR-quality risk analysis®.
Until one knows all the threats to information assets, the vulnerabilities that exist within those assets, and the strength of the controls that are currently in place to protect that information, one cannot prioritize risk response activities and minimize the likelihood and impact of a breach. A risk analysis will identify the gaps in your security program that have might have otherwise been missed and prevent breaches that would otherwise occur. Furthermore, in the case of a reportable breach, it will demonstrate diligent efforts to comply with the regulations and protect sensitive information and thereby reduce the potential penalties.
Conclusion
Protecting healthcare information, and doing so in a comprehensive, by-the-book manner may be viewed as a large investment, but as both OCR and State AGs are making clear, it is not an optional activity. The cost of identifying and responding to risks is far less than that of the monetary penalties and the price of the irreparable reputational damage. This cost is in addition to the pain and distraction that occur from responding to civil lawsuits and actions by OCR and State AGs. If there was ever a time to mature your HIPAA compliance and cybersecurity program, that time is now.
[1] https://www.hhs.gov/hipaa/for-professionals/compliance-enforcement/state-attorneys-general/index.html [2] Ibid.

OCR-Quality Risk Analysis®
Clearwater delivers solutions to hundreds of health systems, health partner organizations, medical device manufacturers, and federal institutions nation-wide. Our complete enterprise cyber risk management solution begins with the most comprehensive, industry-proven risk analysis available, as demonstrated by a 100% OCR acceptance rate. Learn more



